SQL Injections: Retrieving Hidden Data and Subverting Application logic.
Hi, everyone. This blog serves to provide insight into how I successfully solved the first two labs on Web Security Academy during my learning path — (Web Security Academy — SQL injection).
What is SQL Injection?
SQL injection is a web security vulnerability that allows an attacker to interfere with an application’s queries to its database. It allows an attacker to view data that they are not normally able to view.
Examples of SQL Injection
There are multiple examples of SQL Injections. Two of which are:
Retrieving hidden data, where you can modify an SQL query to return additional results.
Subverting application logic, where you can change a query to interfere with the application’s logic.
Lab#1: SQL injection vulnerability in WHERE clause allowing retrieval of hidden data

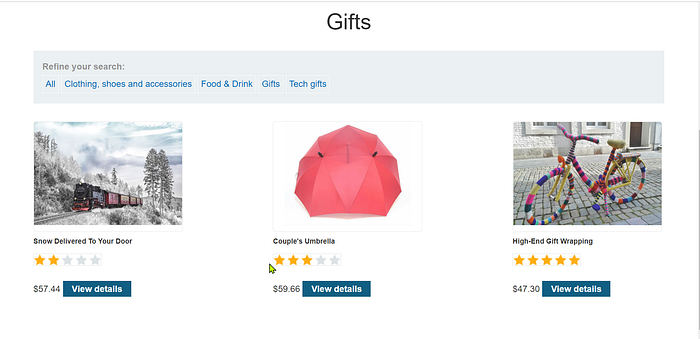
For this lab, the aim is to be able to view all of the products in a category using an SQL Injection with the WHERE clause. I chose the category ‘Gifts’. On my initial browsing of this category, I only discovered three products.
With the use of the Burp Suite Community Edition, I selected Proxy → Intercept is on to be able to Inject the SQL: Gifts’+OR+1=1- -.
Injecting this SQL allows for the statement of (1=1) which is always true in addition to the double dash (- — ) which is a comment indicator and allows for the remainder of the query to be interpreted as a comment thus revealing all of the products compared to the original query of ‘Gift’ AND released = 1 which would only reveal the released products in Gifts.

Below is the results of being able to see both revealed and unrevealed products in the Gifts category after the SQL injection.

Lab#2: SQL injection vulnerability allowing login bypass

This lab allowed me to login into user ‘administrator’ and access the site by entering the credentials of a username administrator and an invalid password.

I achieved this by opening Burp Suite and selecting Proxy →Intercept is on, and Injecting the SQL: administrator’ — -, in line 22.

After injecting the SQL comment sequence, I selected forward until I no longer had the option to forward the SQL and I was successfully logged in as administrator.

These two labs were insightful and after multiple attempts and research, I was able to successfully solve the labs. I am now more knowledgeable of how to Retrieve Hidden Data by modifying the SQL ‘WHERE’ clause with a Boolean statement that would always be true and the comment sequence (- -) and Subverting Application logic by modifying the user parameter with SQL injection comment sequence (‘ — -) thus enabling login bypass.
